Amazon Web Services (AWS) is a cloud computing platform that provides a lot of different services completely managed by AWS. Companies like Netflix, Airbnb, NASA, and various others use AWS to manage their services. Services can be divided into the following sections:
Compute
Storage
Components for Event-Driven Architecture
Load Balancers
Gateways
CI/CD
Monitoring
Each of the sections above contains various services. Having a lot of services also makes them vulnerable to various security threats. Additionally, you may also need efficient control and provisioning of these services to different users. So to address these concerns, AWS offers a complete standalone section called IAM (Identity and Access Management). IAM enables the account owner to have full control over all the resources and services in a highly efficient manner.
The root user is the owner of the account and has access to everything, from basic to large services, that can result in substantial billing. Therefore, It is best practice to manage all the services efficiently using IAM.
IAM Concepts
Following are some of the IAM concepts:
Users
Users are the people that have the access to your AWS services. You can create as many users as you like. It is normally considered a best practice to not use your root user for day-to-day tasks, as it has all the administrative accesses. Instead, create and use the IAM user.
Policies
When talking about the users, there must be some mechanism to have control over the users. Policies get very handy in this situation. Policies define the permissions that are allowed to the assigned user. We can apply the policies to a single user or a whole group.
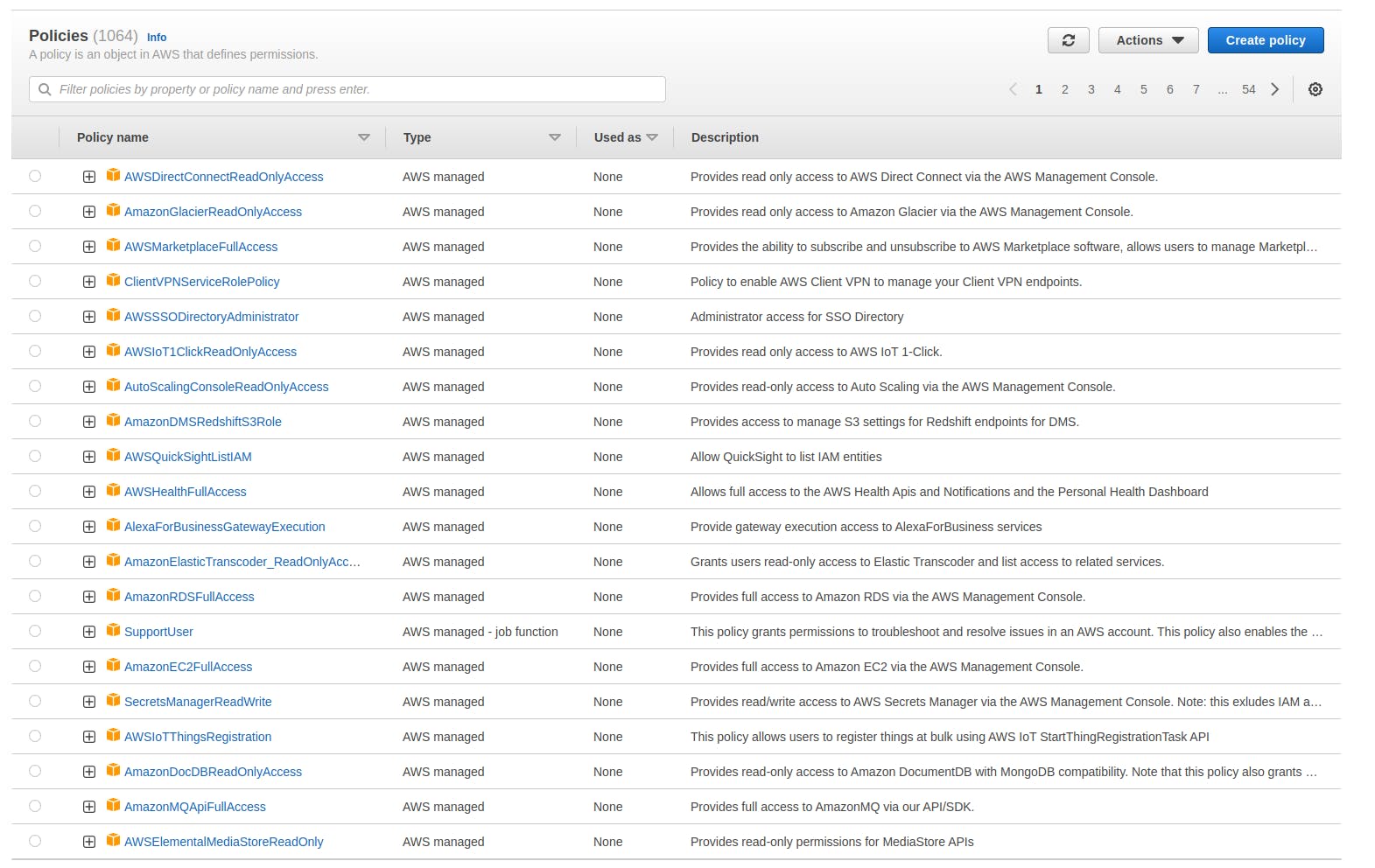
Groups
The users that we have discussed above can be divided into different groups to easily manage the permissions and roles. Imagine having 100s of users and managing the roles and permissions for each of those individually. Groups create a logical separation. Any permission or role assigned to a group will be applied to all users in it. Companies usually create different groups let's say for devs, QA resources, or the infrastructure guys there will be separate groups according to the required permissions.
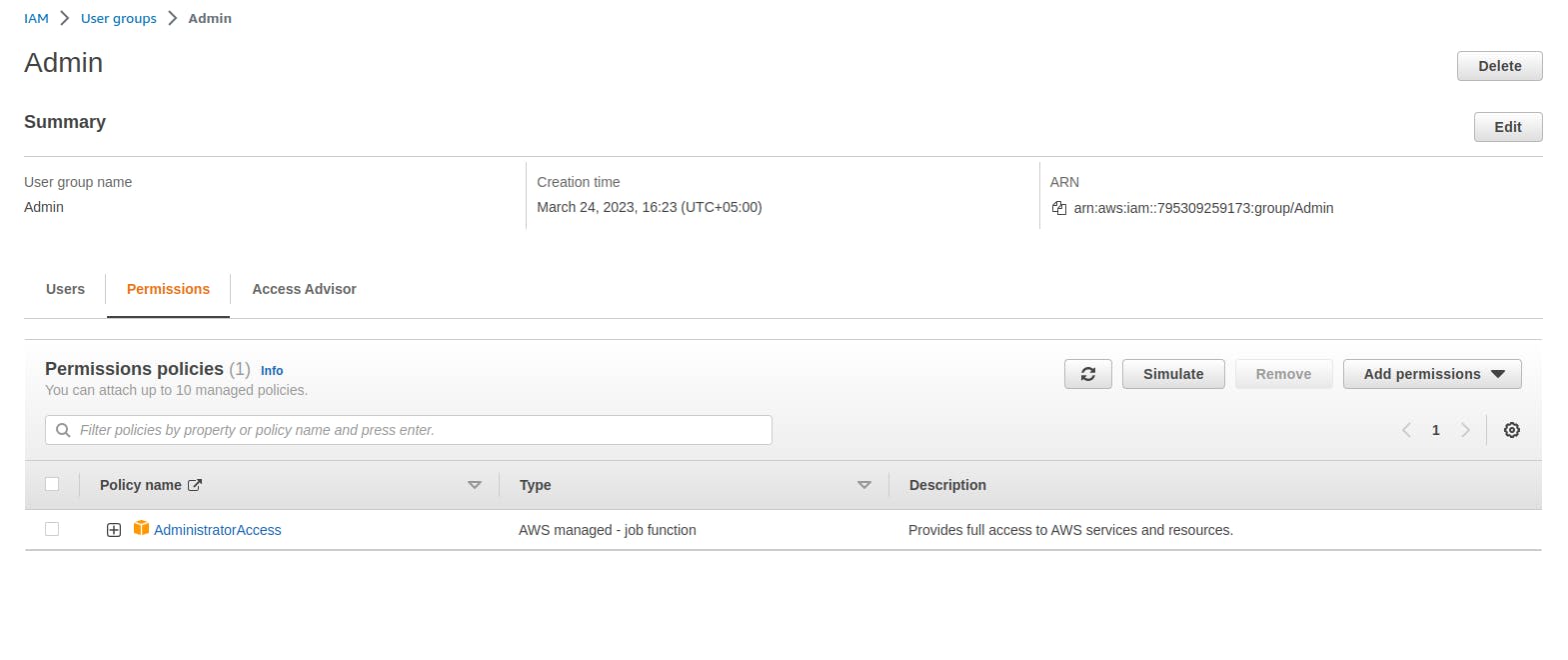
The group mentioned above is assigned the 'AdministratorAccess' policy. Any user assigned to this group will have all the administrator permissions.
Security
Security is just the aspect of making sure that the access to the AWS resources and services is secure. It includes a different mechanism for securing the users such as passwords, or MFA that includes virtual MFA devices, or Physical MFA devices.
Access Keys
It is another way to access AWS resources and services programmatically. Each user can generate its access key so that the resources can be accessed via CLI in most cases.
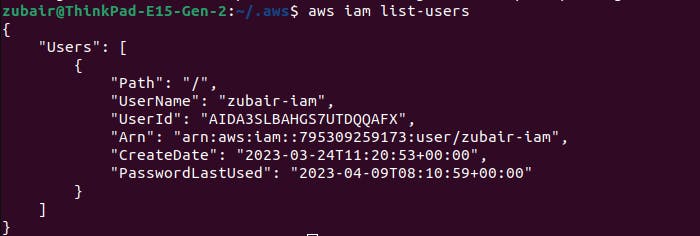
For this make sure to set the access key first for the user then set the AWS credentials on the CLI according to your OS. For Linux, you can run the following command. This will prompt you to enter the following details:
Access Key Id
Access key password
Region Name > Choose any region you would like to have your services in. Please go through the AWS regions detail for more information.
Output Format > You can leave it empty
aws configure
IAM Tools
IAM Access Advisor
It shows the overall information about the permissions granted to the account users and their activities.
IAM Best Practices:
Use the IAM user for daily tasks
Enforce policies to groups and users for controlled access
Use a strong password policy such as MFA
